Cryptography: Difference between revisions
No edit summary |
No edit summary |
||
| (32 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
Cryptography is the science of using codes and ciphers to conceal information. Cryptology is the study of cryptography. Codes and ciphers are terms that are often used interchangeably, but they are distinctly different. A code replaces one piece of information for another entirely different piece of information where the meaning of both is known to both the sender and recipient. A common example of this may be using a phrase such as ''We have contact'' to mean ''We have found the thing we're looking for''. A cipher, on the other hand, modified the information itself to obscure its meaning. A cipher also conceals information but does so by changing the original information (plain text) to cipher text (sometimes referred to as 'black text'). The Polybius Cipher, described below, is an early example of a substitution cipher. | |||
A timeline of cryptography through the middle ages may be found on the [http://crypto.houseblueheron.com/timeline.php House Blue Heron cryptography website] | |||
<ref>Baun, Kevin W. “Cryptography Timeline.” History of Cryptography, February 17, 2020. http://crypto.houseblueheron.com/timeline.php.</ref>. | |||
[[File:Porta.jpg|center|200px|Porta's (photograph by Kevin Baun, sca Melchior zum grauen Wolf) ]] | |||
==Transposition Ciphers== | |||
A transposition cipher moves elements of the plain text and reorders the message so that it is unreadable without knowing the pattern<ref>Baun, Kevin W. “Transposition Ciphers.” History of Crypto. Accessed February 17, 2020. http://crypto.houseblueheron.com/transposition.php.</ref>. | |||
Example: | |||
This is a rail fence cipher | |||
T I A E C E | |||
H S S R I F N E I H R | |||
I A L C P | |||
TIAECE HSSRIFNEIHR IALCP | |||
==Substitution Ciphers== | |||
A wide variety of substitution ciphers were used through the SCA Period. More information on the basic operation of substitution ciphers can be found on the [http://crypto.houseblueheron.com/substitution.php House Blue Heron cryptography website]<ref>Baun, Kevin W. “Substitution Ciphers.” History of Cryptography, February 17, 2020. http://crypto.houseblueheron.com/substitution.php</ref>. | |||
===Polybius Cipher=== | |||
This grid cipher substitution cipher is attributed to the Cleoxenus and Democleitus but was improved by and so attributed to Polybius in ''The Histories'' <ref>Citation needed</ref>. The basic operation of the 5x5 grid is to find the row and collum of each letter to produce an index value. Each index will have exactly two numbers for its index so spacing is not relevant to the code itself. | |||
{| class="wikitable" | |||
|- | |||
! !! 1 !! 2 !! 3 !! 4 !! 5 | |||
|- | |||
| 1 || A || B || C || D || E | |||
|- | |||
| 2 || F || G || H || I/J || K | |||
|- | |||
| 3 || L || M || N || O || P | |||
|- | |||
| 4 || Q || R || S || T || U | |||
|- | |||
| 5 || V || W || X || Y || Z | |||
|} | |||
Example: | |||
A T L A N T I A | |||
11 44 31 11 33 44 24 11 | |||
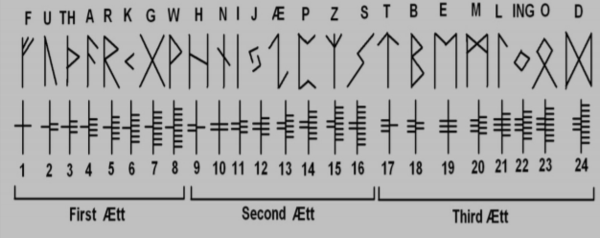
==Runic Ciphers== | |||
[[File:hahalruna.png|center|600px|Runic cipher index system ]] | |||
=Notes= | |||
<references /> | |||
[[Category:Arts and Sciences]] | |||
Latest revision as of 07:54, 31 May 2022
Cryptography is the science of using codes and ciphers to conceal information. Cryptology is the study of cryptography. Codes and ciphers are terms that are often used interchangeably, but they are distinctly different. A code replaces one piece of information for another entirely different piece of information where the meaning of both is known to both the sender and recipient. A common example of this may be using a phrase such as We have contact to mean We have found the thing we're looking for. A cipher, on the other hand, modified the information itself to obscure its meaning. A cipher also conceals information but does so by changing the original information (plain text) to cipher text (sometimes referred to as 'black text'). The Polybius Cipher, described below, is an early example of a substitution cipher.
A timeline of cryptography through the middle ages may be found on the House Blue Heron cryptography website <ref>Baun, Kevin W. “Cryptography Timeline.” History of Cryptography, February 17, 2020. http://crypto.houseblueheron.com/timeline.php.</ref>.

Transposition Ciphers
A transposition cipher moves elements of the plain text and reorders the message so that it is unreadable without knowing the pattern<ref>Baun, Kevin W. “Transposition Ciphers.” History of Crypto. Accessed February 17, 2020. http://crypto.houseblueheron.com/transposition.php.</ref>.
Example:
This is a rail fence cipher
T I A E C E
H S S R I F N E I H R
I A L C P
TIAECE HSSRIFNEIHR IALCP
Substitution Ciphers
A wide variety of substitution ciphers were used through the SCA Period. More information on the basic operation of substitution ciphers can be found on the House Blue Heron cryptography website<ref>Baun, Kevin W. “Substitution Ciphers.” History of Cryptography, February 17, 2020. http://crypto.houseblueheron.com/substitution.php</ref>.
Polybius Cipher
This grid cipher substitution cipher is attributed to the Cleoxenus and Democleitus but was improved by and so attributed to Polybius in The Histories <ref>Citation needed</ref>. The basic operation of the 5x5 grid is to find the row and collum of each letter to produce an index value. Each index will have exactly two numbers for its index so spacing is not relevant to the code itself.
| 1 | 2 | 3 | 4 | 5 | |
|---|---|---|---|---|---|
| 1 | A | B | C | D | E |
| 2 | F | G | H | I/J | K |
| 3 | L | M | N | O | P |
| 4 | Q | R | S | T | U |
| 5 | V | W | X | Y | Z |
Example:
A T L A N T I A 11 44 31 11 33 44 24 11
Runic Ciphers
Notes
<references />